In this Cisco CCNA training tutorial, you’ll learn about Spanning Tree Portfast, BPDU Guard, and Root Guard. Scroll down for the video and also text tutorial.
Cisco Portfast, BPDU Guard, and Root Guard Video Tutorial

Armand Picari

I watched your course and I passed my CCNA. Now I am working for the network team in my company. Thank you for the great videos!
Spanning Tree Portfast
Portfast can take up to 50 seconds for Spanning Tree to transition a port to a forwarding state when that port becomes active by powering on the switch or plugging a network cable into it. If you think about it, a loop cannot be formed on ports where a single end host is plugged in.
In the diagram below, I do have a potential loop between my three switches there, so one of the ports was put into a blocking state. I then go and plug a PC into one of the switches with a single network cable connecting it, well, it's impossible to have a loop going through there as long as it doesn't change.
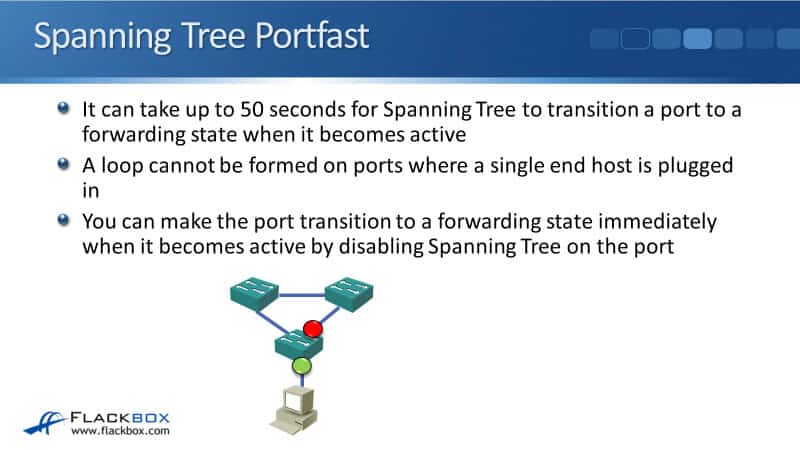
It would be nice if we didn't have to wait 50 seconds for the port to come up and we can actually configure that. We can make the port transition to a forwarding state immediately when it becomes active by disabling the Spanning Tree on the port.
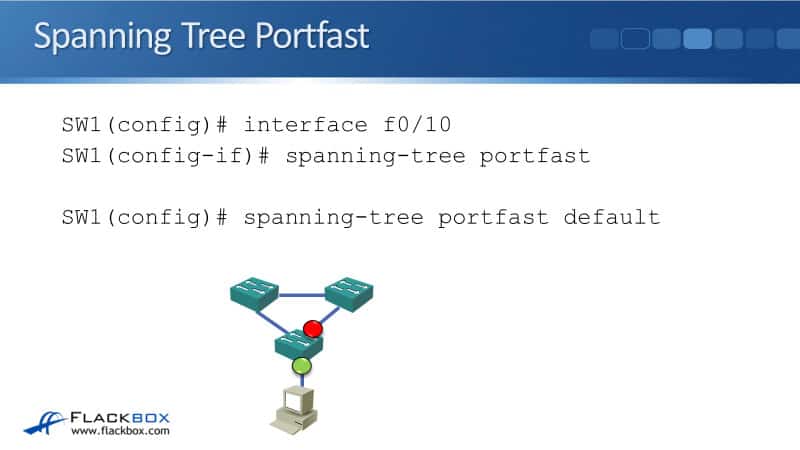
We can do that with the Portfast command. This is configured at the interface level. Since my PC is plugged in interface F0/10, we enter the command:
interface f0/10
spanning-tree portfast
The command disabled Spanning Tree from running on the port and it will transition to forwarding immediately. You can also set all of your ports to be in Portfast by default. To do that, at global configuration mode, we enter the command:
spanning-tree portfast default
Then, to make sure that on any ports that are connected to switches, we enter this command on these ports:
no spanning-tree portfast
Spanning Tree BPDU Guard
There could be a big problem though, if you enable Portfast on a port, you're disabling Spanning Tree. If a loop is formed through it, then you're going to get a broadcast storm.
The most common reason is users doing things they shouldn't be doing like adding devices to the network, adding switches, or changing the cabling. You can see that's what happened in the diagram below.
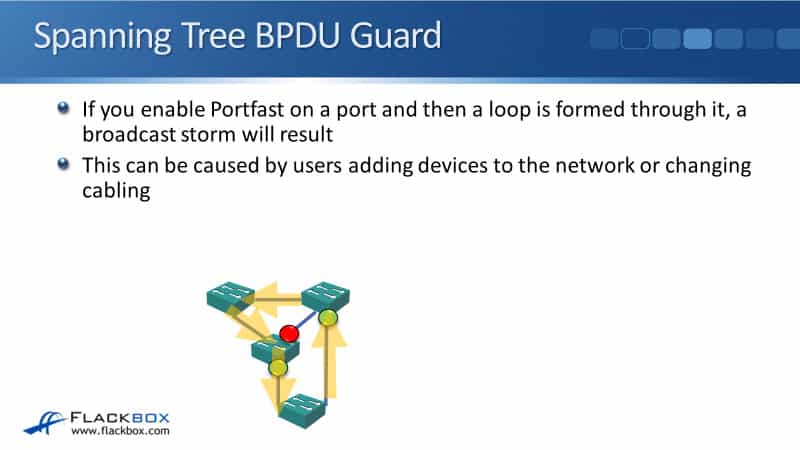
We've got our switches up at the top are configured with Portfast and we expect normally that it would be end hosts that get plugged in there. But probably what happened was for some part of a building there were not enough wall ports.
So, a user has come in with their own switch and they've plugged that into two different wall ports in that part of the office to get more ports for the additional users. By doing that, they've formed a loop and now you're going to get a broadcast storm.
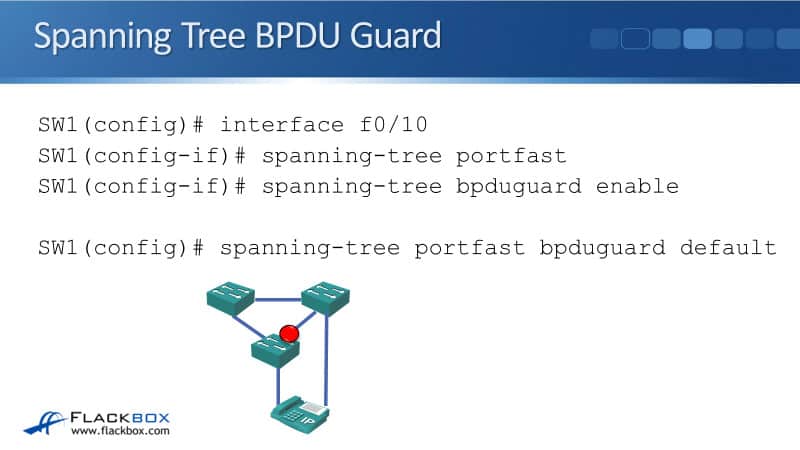
It’s dangerous enabling Portfast, therefore, we want to take some mitigation against this kind of problem happening and that is where BPDU Guard comes in. You can enable BPDU Guard on the same interfaces where you've enabled Portfast. Then, if a BPDU is received, the port will be shut down.
When switches come online, they send BPDUs at all ports to build the Spanning Tree. So if you do plug a switch into a port, it will receive a BPDU on there and this can allow you to switch to automatically shut down that port to prevent a loop from happening.

The command to enable BPDU Guard is:
spanning-tree bpduguard enable
It is best practise to use these commands on your networks where you've got ports that the end hosts are going to be plugged into. Just like we could with Portfast, you can also make BPDU Guard the global default. To do that in global config, we use the command:
spanning-tree portfast bpduguard default
Spanning Tree Root Guard
Another Spanning Tree command to cover is Root Guard and this is used for a different reason than Portfast and BPDU Guard are. Spanning Tree Root Guard prevents an unintended switch from becoming the root bridge.
For example, you have an old switch which had been in a different office and it happened to be the root bridge in that different office, but it's a much older switch than the root bridge which is in your main office.
You get that old switch shipped back to the main office, then you didn’t do a factory reset and you plugged it into the network. It happens to have a higher priority than the current root bridge. Now, that old switch is going to become the root bridge and you want to make sure that this should not happen.
Another reason that the wrong switch could become a root bridge is maybe that you're under an attack. What the attacker will do is put a switch in the network, trying to make that the root bridge to force traffic to come through the switch that they're controlling. They'll then be able to sniff the traffic and gain access to sensitive information.
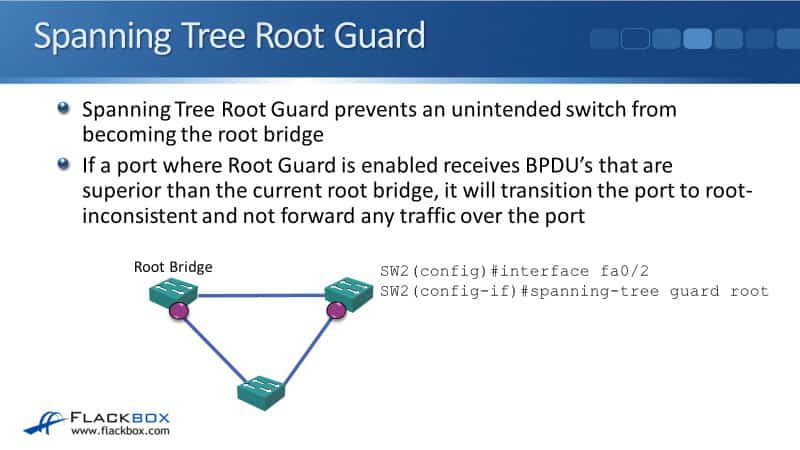
So, if you want to make sure that the current root bridge remains your root bridge, you can use Root Guard to help ensure that. The way it works is if a port was Root Guard is enabled when it receives BPDUs that superior to the current root bridge, it will transition that port to root-inconsistent.
There will be no traffic forwarded over that port. The way that you configure this is on the interface configuration mode, you enter the command:
spanning-tree guard root
In our example, we've got our root bridge up in the top left. This is the one that we want to remain the root bridge. What we do is on the port connected to the bottom switch in the Root Bridge and SW2, we configure Root Guard.
Now, if a switch at the bottom starts sending out superior BPDUs, they are not going to be accepted and the port that is connected to that switch is going to be transitioned to root-inconsistent, basically shutting the port down.
Portfast and BPDU Guard Configuration Example
This configuration example is taken from my free ‘Cisco CCNA Lab Guide’ which includes over 350 pages of lab exercises and full instructions to set up the lab for free on your laptop.
Click here to download your free Cisco CCNA Lab Guide.
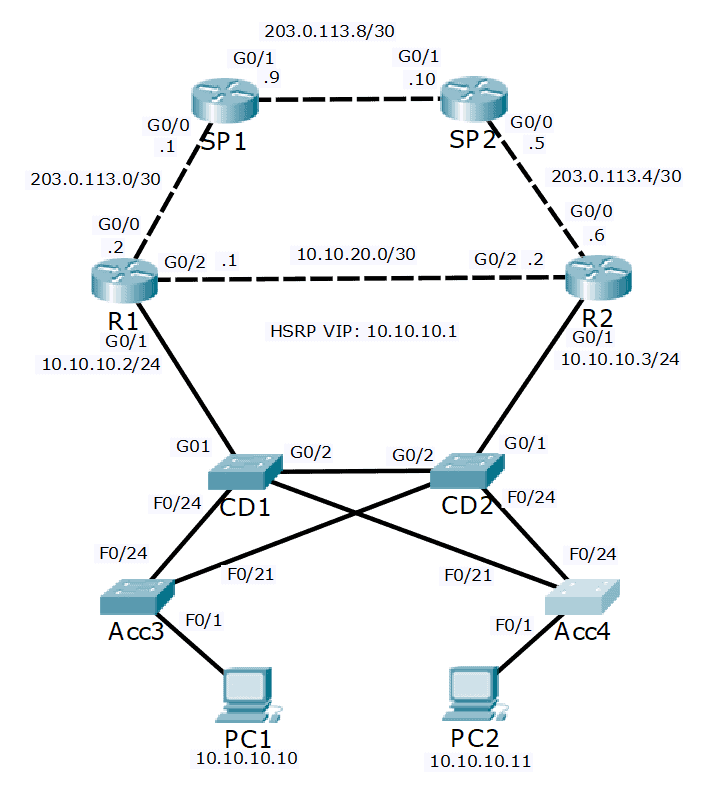
- A Layer 2 loop cannot be formed on a port where a single end host is connected. Disable spanning tree on these ports.
You are concerned that a user may introduce a loop into the network by adding additional switches or changing the cabling. Also ensure that the ports where Spanning Tree is disabled will be automatically shut down if a switch is detected on the other side of the link.
Acc3(config)#int f0/1
Acc3(config-if)#spanning-tree portfast
Acc3(config-if)#spanning-tree bpduguard enable
Acc4(config)#int f0/1
Acc4(config-if)#spanning-tree portfast
Acc4(config-if)#spanning-tree bpduguard enable
CD1(config)#int g0/1
CD1(config-if)#spanning-tree portfast
CD1(config-if)#spanning-tree bpduguard enable
CD2(config)#int g0/1
CD2(config-if)#spanning-tree portfast
CD2(config-if)#spanning-tree bpduguard enable
Additional Resources
Spanning-Tree RootGuard: https://networklessons.com/spanning-tree/spanning-tree-rootguard
What is BPDU Guard and how to configure BPDU Guard in Cisco Switches: https://www.omnisecu.com/ccna-security/what-is-bpdu-guard-and-how-to-configure-bpdu-guard-in-cisco-switches.php#:~:text=in%20Cisco%20Switches-,What%20is%20BPDU%20Guard%20and%20how%20to%20configure%20BPDU%20Guard,BPDU%20from%20its%20connected%20device.
Configuring Spanning Tree PortFast, BPDU Guard, BPDU Filter, UplinkFast, BackboneFast, and Loop Guard: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/stp_enha.html
Libby Teofilo

Text by Libby Teofilo, Technical Writer at www.flackbox.com
Libby’s passion for technology drives her to constantly learn and share her insights. When she’s not immersed in the tech world, she’s either lost in a good book with a cup of coffee or out exploring on her next adventure. Always curious, always inspired.