In this NetApp tutorial, you’ll learn about ONTAP VLANs. Scroll down for the video and also the text tutorial.
NetApp ONTAP VLANs Tutorial
Casey Cockfield

Your NetApp training courses saved my job. All the Engineers left except me, and without your training I would have failed. Without your course, being thrown into NetApp so swiftly as an entire European cluster failed… I would have been in a big big mess! Thank you so much brother… You saved my career!
We can use VLANs in ONTAP to share our physical network ports among different client connection types but keep those connections still separate and secure from each other. In the ideal scenario, different connection types would be terminating on different physical ports.
For example, let's say that we've got DeptA and DeptB, we've created a separate SVM for DeptA and DeptB, and both departments are using CIFS, NFS, iSCSI and have got their Management traffic as well.
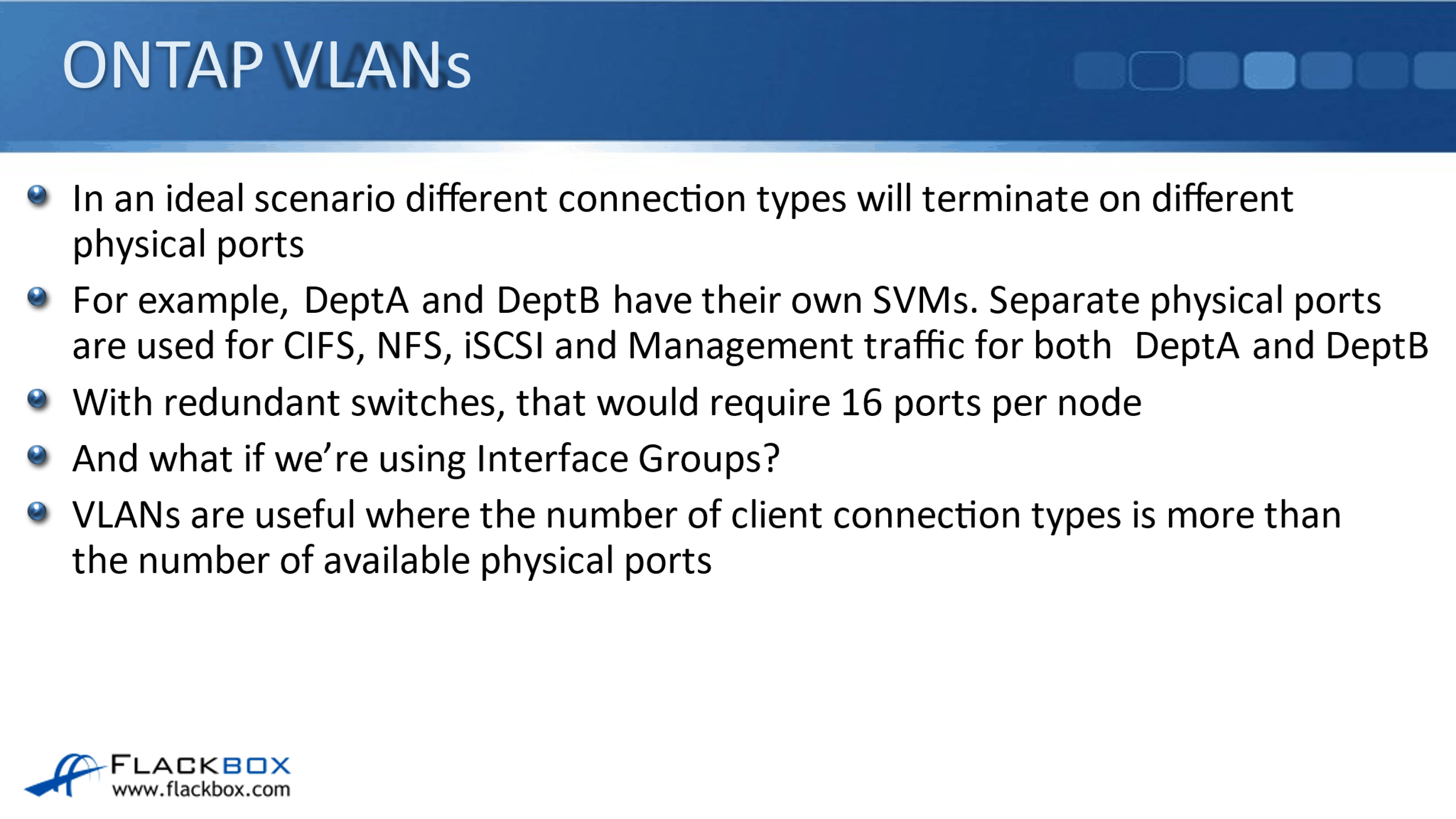
If we wanted to keep those CIFS connections, NFS, iSCSI, and Management connections on separate physical ports for the two different SVMs, and we were connecting out to two redundant switches, well, we would need 16 physical ports per node for that scenario. And if we were using interface groups to bundle our physical ports, we would need even more.
So, it's not always going to be possible to dedicate separate physical ports to the different connection types. Actually, very often, it wouldn't be possible to do that. So, VLANs are useful where the number of those client connection types is more than the number of available physical ports.
A VLAN can be created on a physical port or on an interface group, and LIFs, that's our logical interfaces, and that's where the IP addresses are signed. They can be placed on physical ports or interface groups or on VLANs.

Dedicated Physical Ports
Looking at using dedicated physical ports first, this is where we do have separate, dedicated physical ports for our different connection types. We've got a DeptA SVM, and we've got a DeptB SVM. We're using physical port e0c for DeptA. So, DeptA has got a logical interface with IP address 10.10.10.10, and it is homed on port e0c.
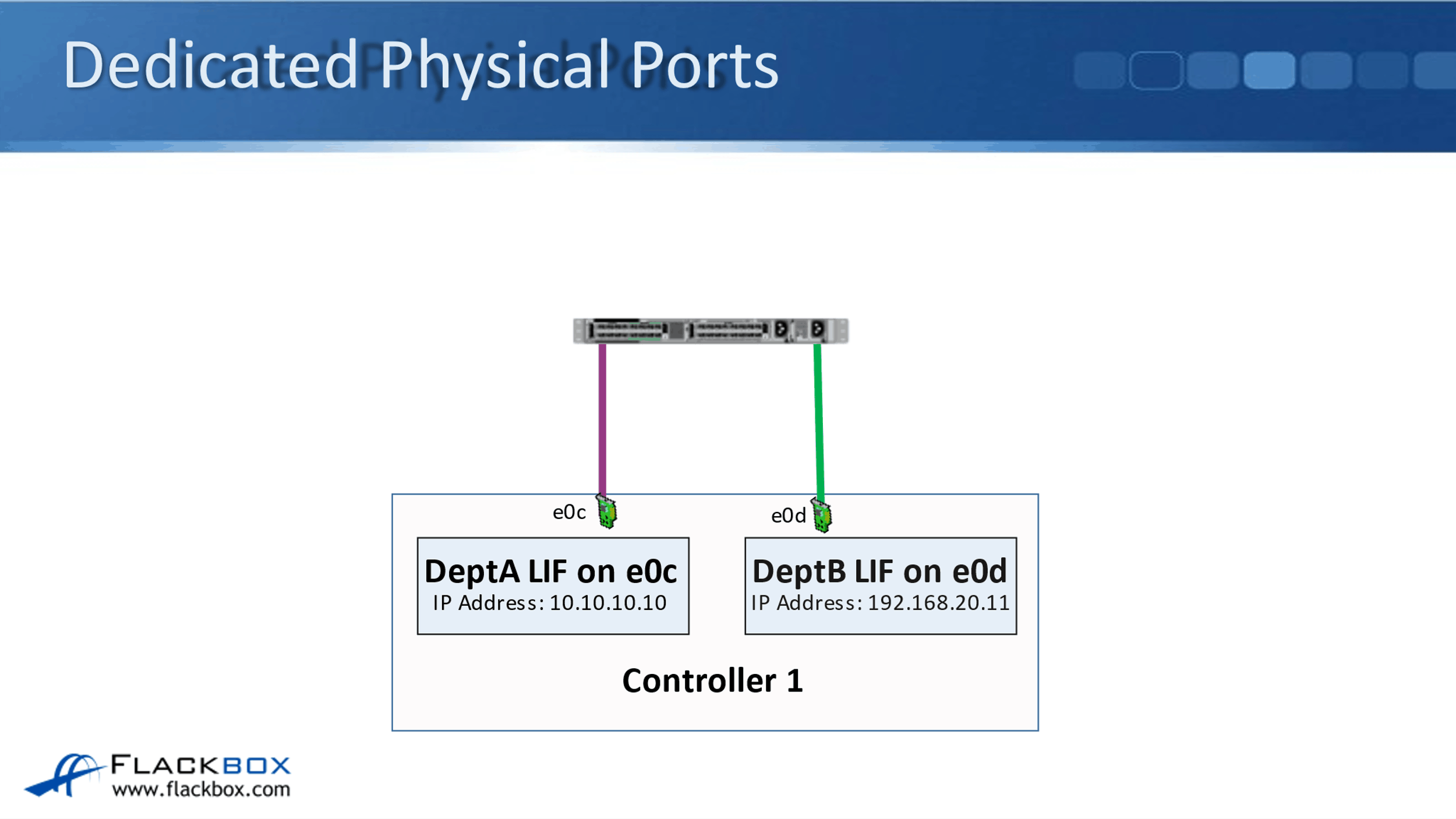
Then DeptB, they've got a logical interface with IP address 192.168.20.11, and it is homed on port e0d. As long as each of these physical ports had enough bandwidth to support the client, then that would be the ideal way to configure this particular scenario.
VLANs
But maybe we don't have enough physical ports to give both DeptA and DeptB their own ports for this particular connection type. Well, in that case, they can share the same underlying physical port. So now, on port e0c on my node, I'm going to run the traffic for both DeptA and DeptB on that physical port.
Obviously, they are two different departments. I need to keep them secure from each other. So the way I do that is at Layer 3 of the OSI model, we're using different IP addresses. DeptA's logical interface is using IP address 10.10.10.10. DeptB's logical interface is using IP address 192.168.20.11. So, they are in different IP subnets.
Therefore, on my routers and my firewalls outside the ONTAP system, I can create rules there that keep those two different traffic types separate from each other. So the IP address level, I've got them separated at Layer 3 of the OSI stack.
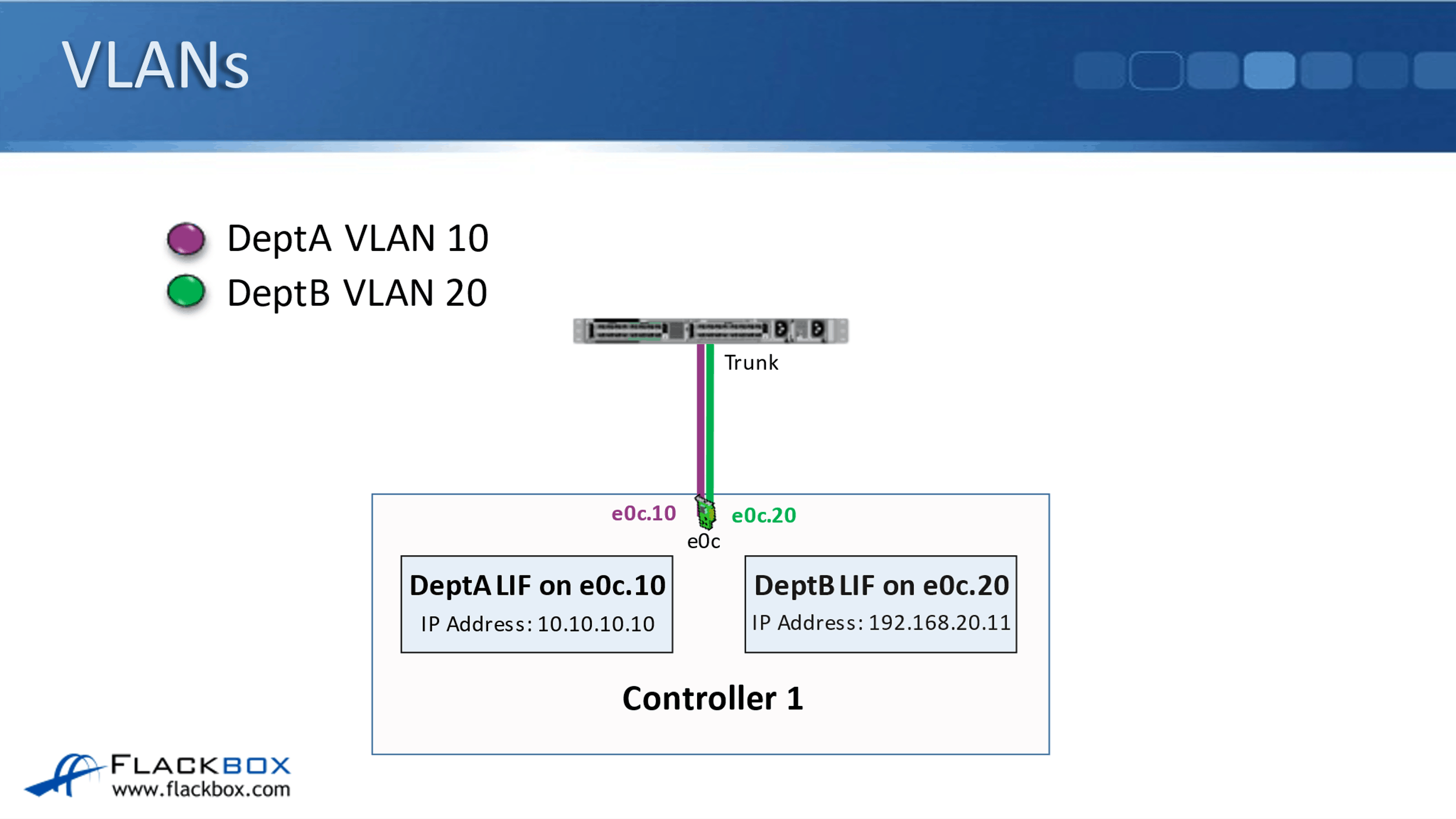
I also want to have them separated at Layer 2 of the OSI stack as well, so that's why I put them into separate VLANs. DeptA are using VLAN 10 in our example, and DeptB are using VLAN 20 in our example. So, that makes sure that from my networking point of view DeptA and DeptB are kept strictly segregated from each other.
On the switch port that is connecting down into my ONTAP node, I configured that as a trunk. A trunk port will carry the traffic for both VLAN 10 and for VLAN 20. When traffic is tagged with VLAN 10, that's going to hit my VLAN interface that I've created for DeptA.
So for DeptA, I create an e0c.10 VLAN interface, meaning any traffic that is tagged for VLAN 10 is going to hit that logical interface, and any traffic, which is tagged with VLAN 20, which is for DeptB, is going to hit my VLAN interface e0c.20.
I put my DeptA logical interface on the e0c.10 VLAN interface and I put my DeptB logical interface with their IP address on the e0c.20 VLAN Interface. So, that allows both DeptA and DeptB to share the same underlying physical port, but their traffic is kept separate and secure from each other.
Interface Groups
That first example was using physical ports. What if I have grouped my physical ports into an interface group? So on the first slide here, it's where I have got separate interface groups for DeptA and DeptB. Here on my Node 1, physical port e0c and e1a are grouped into an interface group.
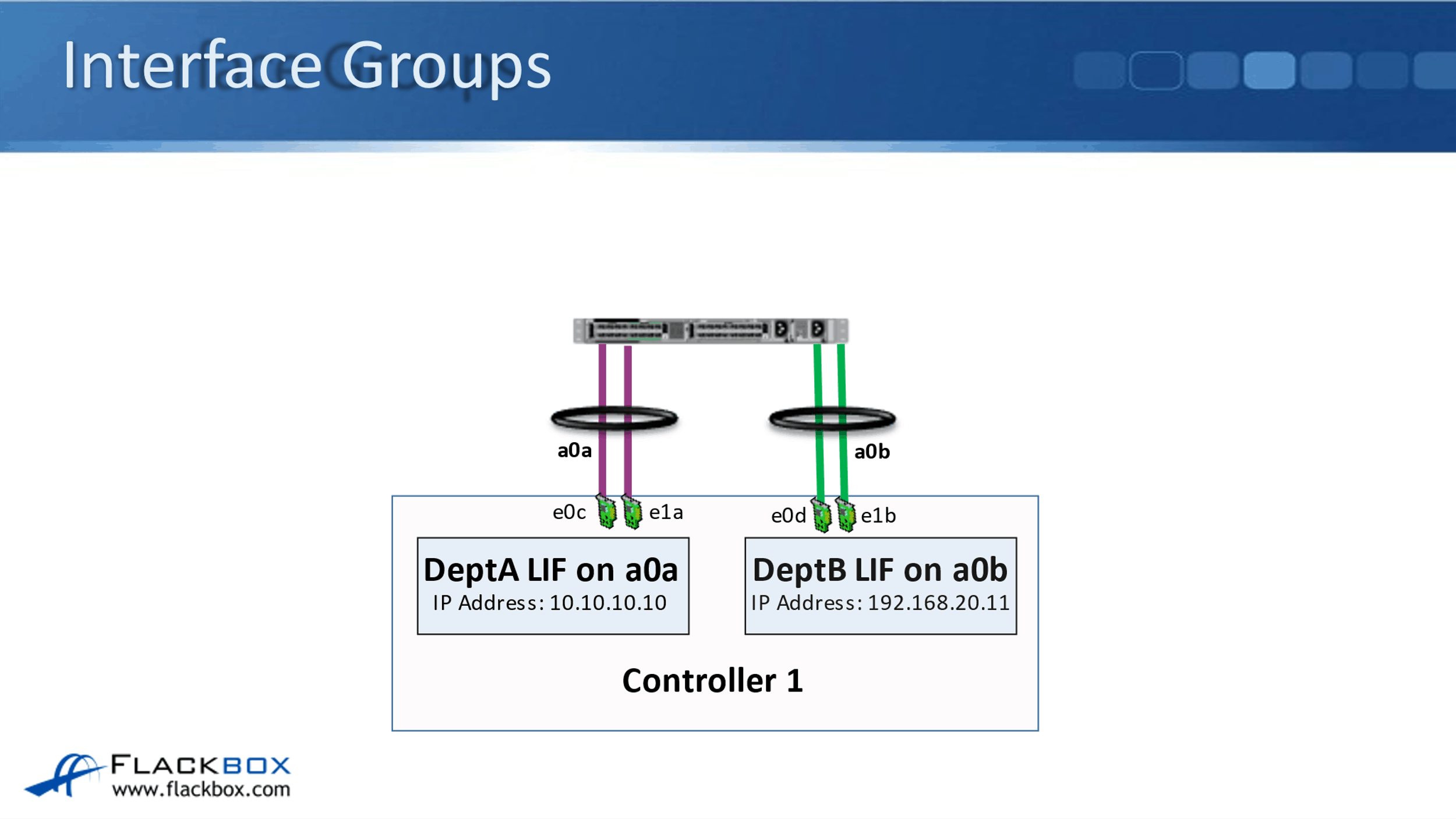
Notice that that is using one physical port, which is on board on the controller. The other one is using a physical card in slot one, that is e1a. Then on that interface group, I've grouped that into interface group a0a, and my DeptA logical interface with IP address 10.10.10.10 is placed on that interface group.
Then, I have configured a separate interface group for DeptB that is on physical ports e0d and e1b. They've been bundled into the logical interface group of a0b, and my DeptB logical interface with IP address 192.168.20.11 is put on interface group aob. So here, I've got separate interface groups dedicated for DeptA and for DeptB.
Interface Group and VLANs Combined
Let's look and see where we can use VLANs here. So maybe there wasn't enough bandwidth really there for DeptA and DeptB to burst. Let's say that I'm using 1 gigabit ethernet ports here. So here, DeptA and DeptB have both got 2 gigabits available to them, but maybe sometimes DeptA burst a little bit above that, and maybe sometimes DeptB burst a bit above that as well.
Well, here, we are physically limited to the maximum of 2 gigabits, so they wouldn't be able to burst above it. Let's look and see how we can use VLANs to allow them to occasionally burst above that 2 gigabits. So here, now I take my four interfaces on node one, e0c, e1a, e0d, and e1d, and I put those all into a single interface group now of a0a.
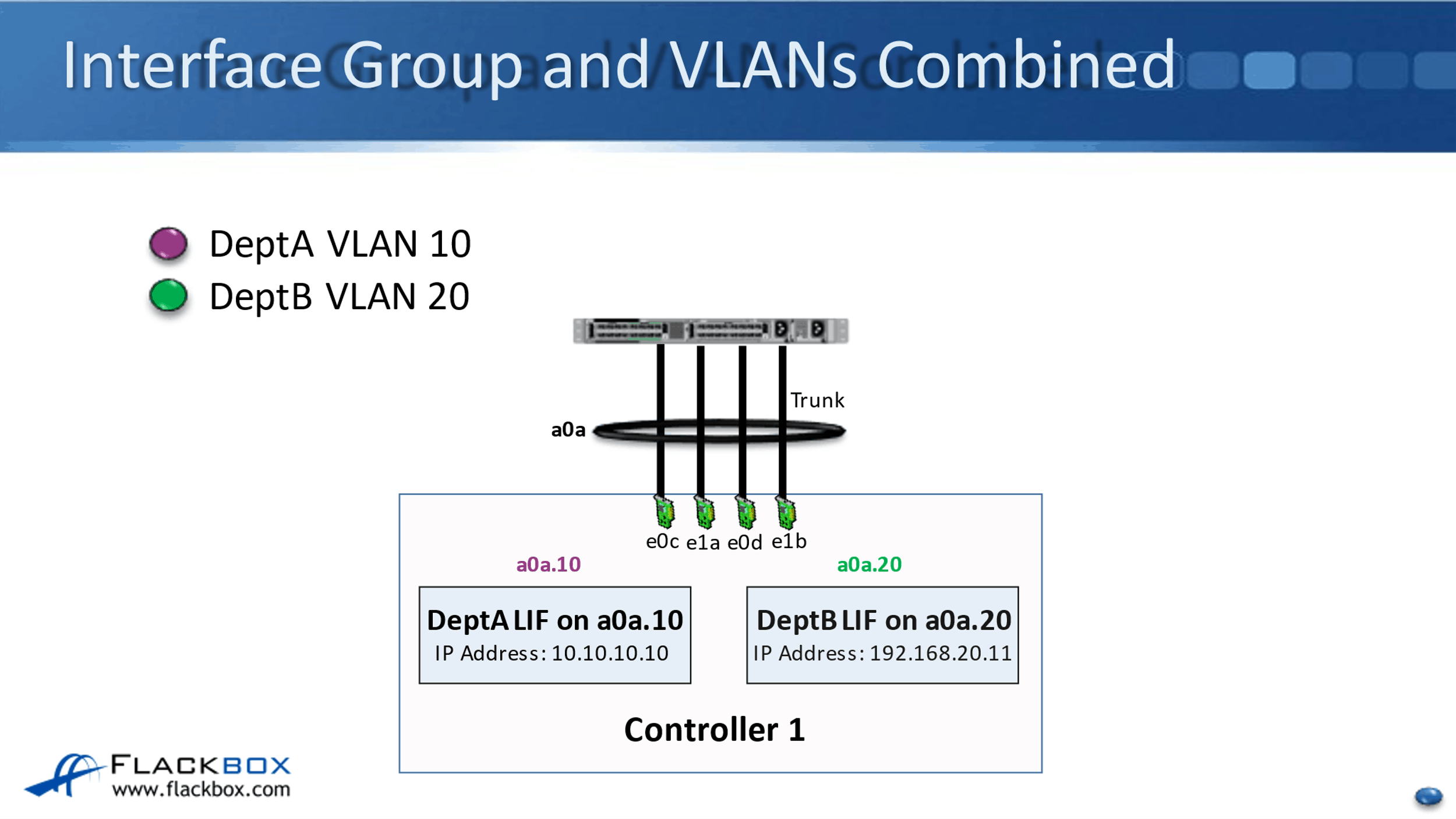
Then, I split my interface group of a0a into my two different VLAN interfaces, that's a0a.10 for VLAN 10 and a0a.20, which is for VLAN 20. DeptA's logical interface with IP address 10.10.10.10 goes on to my a0a.10 VLAN interface, and Dept B's logical interface with IP address 192.168.20.11, that goes onto the VLAN interface of a0a.20.
Now, you can see that I've got 4 gigabits per second bundled together here into my single interface group logical interface. I'm sharing that with both DeptA and DeptB. So now, if either department sometimes wants to burst above the 2 gigabits per second, I've got an aggregate of 4 gigabits per second there, and we're going to be able to do that.
Now, obviously, I need to be careful here that one department doesn't take all of the available bandwidth. Well, I can use storage QoS to do that, but this is a way that we can use VLAN interfaces to allow DeptA and DeptB to be able to burst above what they would have been able to if I was dedicating interface groups to each one. It still keeps them separate and secure from each other.
Additional Resources
How VLANs Work: https://library.netapp.com/ecmdocs/ECMP1368834/html/GUID-EC1DBB08-1B51-4981-A8D9-29835FC0149B.html
Configure VLANs Over Physical Ports: https://docs.netapp.com/us-en/ontap/networking/configure_vlans_over_physical_ports.html
Guidelines for Setting up VLANs in Data ONTAP: https://documents.uow.edu.au/~blane/netapp/ontap/nag/networking/concept/c_oc_netw_vlan-guidelines.html
Libby Teofilo

Text by Libby Teofilo, Technical Writer at www.flackbox.com
Libby’s passion for technology drives her to constantly learn and share her insights. When she’s not immersed in the tech world, she’s either lost in a good book with a cup of coffee or out exploring on her next adventure. Always curious, always inspired.