
In this SAN and NAS Storage tutorial, I cover the iSCSI (Internet Small Computer System Interface) SAN protocol. iSCSI runs over Ethernet networks and was originally designed as a less expensive alternative to Fibre Channel.
It has higher packet overhead and has traditionally been seen as having lower reliability and performance than Fibre Channel does. Scroll down for the video and also text tutorial.
Want the complete course? Click here to get the Introduction to SAN and NAS Storage course for free
iSCSI SAN Overview – Video Tutorial

Steve Charl Tolmay

Great course, I gained so much understanding on this subject. It was fun to listen to and the real world examples are greatly appreciated. Keep up the good job, thank you!
I recommend you check out my Fibre Channel Overview series first to get a good grounding in overall SAN basics before moving on to iSCSI. The series of three videos are available here:
Part One – FCP and WWPN Addressing
Part Two – Zoning, LUN Masking and Fabric Login
Part Three – Redundancy and Multipathing
iSCSI traffic can run over either traditional Ethernet Network Interface Cards (NICs) or TCP Offload Engine (TOE) cards on our hosts. TOE cards are specialist network adapters which offload the storage TCP/IP processing from a server's CPU. They are also known as iSCSI Host Bus Adapters (HBAs).
What is iSCSI?
The iSCSI is a transport layer protocol running over TCP/IP. This IP-based storage networking standard enables you to transfer block-level data to hosts using the SCSI protocol.
iSCSI links data storage facilities and gives TCP the recovery from packet loss. It also supports network packet encryption and decryption.
iSCSI Networks
iSCSI can share the existing Ethernet data network, or have its own dedicated network infrastructure.
In the diagram below we have an example of dedicated network infrastructure for our iSCSI storage traffic.

iSCSI Dedicated Network
We have a web server ‘Server 1’ in the middle of the diagram, and a client up at the top, which wants to open a web page which is hosted on Server 1. The client sends its HTTP request to Server 1 over our standard Local Area Network up at the top.
Server 1 then fetches the webpage from its iSCSI storage down at the bottom using a separate dedicated Ethernet network that is just used for storage.
Server 1 has redundant network connections. It's got two Ethernet NICs connected to the data network at the top facing the client, and a pair of NIC or TOE cards connected to the storage network at the bottom.
In the next diagram below, we have a shared network infrastructure for both servers to storage and server to client traffic. Our normal data and our storage traffic are both going through the same switches and can use the same Network Cards on our end hosts.
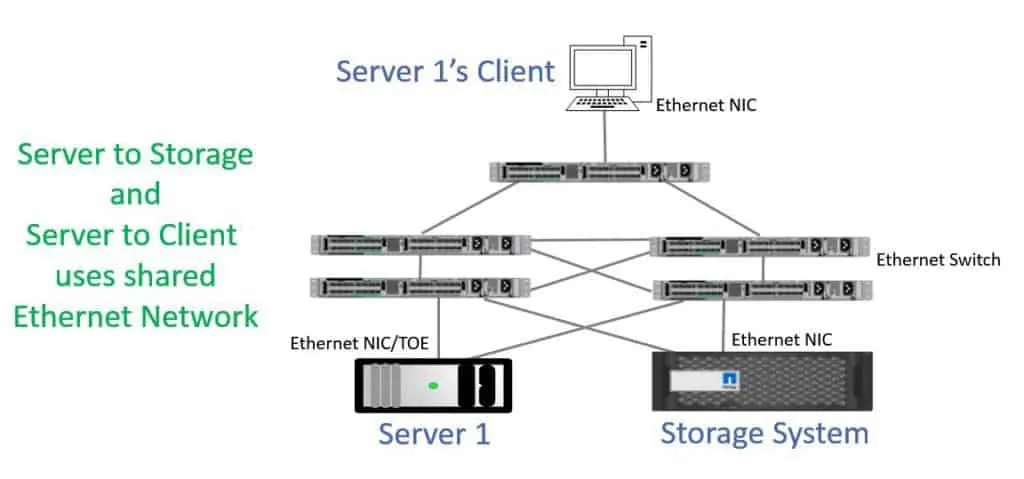
iSCSI SAN Shared Network
If you tried to do this back in the day when we had just 1 Gigabit Ethernet then you could have problems, but it’s more feasible now that we have 10 Gigabit Ethernet and even faster speeds.
If we’re using shared infrastructure, then best practice is to segregate our data and storage traffic into different VLANs for performance and security.
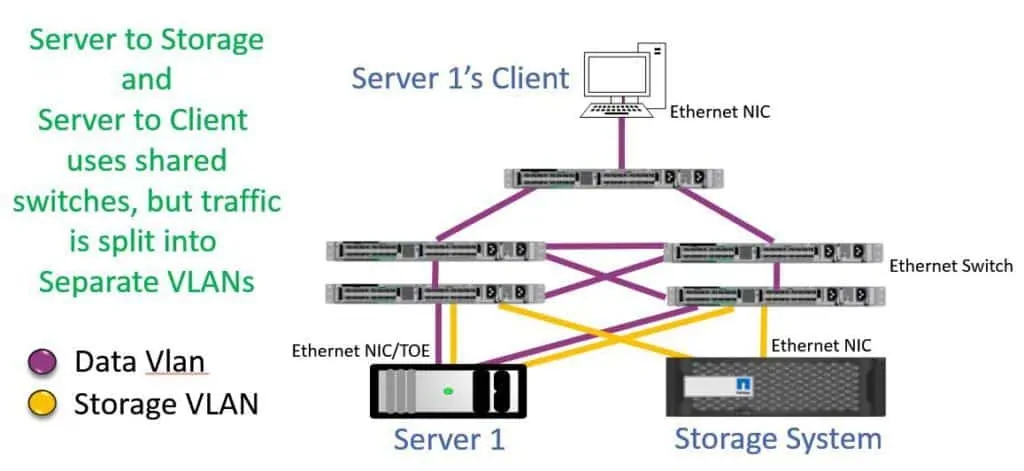
iSCSI SAN with VLANs
On the server, we could have two different physical ports for the data and storage traffic, or we could trunk both VLANs into the same physical part.
For the switch to switch traffic we need to comply with the physically separate ‘Fabric A / Fabric B’ best practice for the storage traffic. The switches will likely be cross-connected for the data traffic. We will have separate ports for the data and storage traffic for this reason and also for enhanced performance and security.
Notice that we've got half the infrastructure here compared to when we used the dedicated storage network. With the dedicated storage network, we had 4 network ports on the server and 4 cables which were connected to 4 switches.
With shared infrastructure, we've got 2 network ports, 2 cables, and 2 switches. Having dedicated infrastructure increases the hardware costs and requires more space, power, and cooling, but can give us more reliability and a simpler VLAN configuration.
iSCSI Main Components
- iSCSI Initiator
An iSCSI initiator could be a hardware device or software residing on the host computer within the storage network that handles communications over the IP network. The initiator connects to the iSCSI target and transfers iSCSI commands as data packets.
- iSCSI Target
iSCSI target is the remote storage device that appears as a local drive to the host. When the iSCSI target receives the data packets from the iSCSI initiator, the iSCSI commands are presented then disassembled in the OS. If the data packets are encrypted at the initiator level, then they are decrypted at the target level.
iSCSI Addressing
Onto the Addressing now. Fibre Channel uses World Wide Names to identify initiators and targets. iSCSI uses iSCSI Qualified Names (IQNs), or less commonly it can use an Extended Unique Identifier (EUIs). The IQN can be up to 255 characters alone, and has the format:
iqn.yyyy-mm.naming-authority:unique name
For example, the IQN could be iqn.1991-05.com.microsoft:testHost. Don't worry if you see a really old date in the IQN. The IQN is derived from when the vendor applied for IQN addresses, so it’s common for it to be an old date. The IQN is assigned to the host as a whole similar to the way the WWNN is applied in Fibre Channel.
iSCSI runs over Ethernet, so individual ports are addressed by IP addresses rather than WWPNs as they are in Fibre Channel. iSCSI does not support Fibre Channel's FLOGI, PLOGI, and PLRI login process.
Therefore, an administrator must explicitly point the initiator at its target by specifying one of the IP addresses in the Target Portal Group. It will then discover the target's IQN and the other ports in the TPG.
Multipathing software on the initiator can then choose which path or paths to take to the target. Multipathing in iSCSI works the same as multipathing in Fibre Channel. Although it runs over Ethernet, iSCSI is still a SAN protocol with multipathing intelligence on the initiator.
LUN Masking is also configured in the same way as in Fibre Channel, but using the IQN rather than the WWPN to identify the client. Zoning is not supported in iSCSI on our switches.
Password-based authentication is typically configured on the initiator and target to guard against spoofing attacks, and end to end IPSec encryption can also be enabled if you need to enhance security further.
What are the Advantages of iSCSI SAN?
iSCSI Storage or SAN is a cost-effective substitute when moving to networked storage. Furthermore, iSCSI SAN can be built on an existing network and it also provides several advantages such as:
- Fast and Efficient data transfer, since it is block-based.
- Flexibility and High Performance.
- Simplified Network Storage Environment and Management.
- Most network storage devices are compatible with iSCSI.
Please watch the video to see a hands-on demonstration of connecting to a LUN from a Windows iSCSI initiator.
Additional Resources
RFC 3720 - Internet Small Computer Systems Interface
Free ‘Introduction to SAN and NAS Storage’ training course
The video is an excerpt from my Introduction to SAN and NAS Storage training. You can get the entire series for free here: