In this Cisco CCNA training tutorial, you’ll see the configuration for SNMP version 3. Scroll down for the video and text tutorial.
SNMP v3 Configuration Video Tutorial

Tanesha Garvey

After taking the CCNA course and the knowledge I gained on the network I excelled in my current role with Comstor / Cisco and was head hunted by Juniper Networks which was a massive success.
In SNMPv1 and SNMPv2, the SNMP Manager (NMS server) and the SNMP Agent (router or switch), recognize each other through simple unencrypted community strings.
SMPv3 is the improved version of the previous two SNMP versions. It is more secured as it supports authentication and encryption. With SNMPv3, the security model uses users and groups.
We're going to configure a user on the router or switch, then we configure a matching user on the NMS server for them to recognize each other.
Most of the settings are configured at the group level. Those settings are going to be applied to the user depending on which group it is actually in.
SNMPv3 Security Levels
There are three different SNMPv3 security levels and these are configured at the group level. Normally, you're going to use just one security level. However, it is possible to have one NMS server in one group with one security level, and a different NMS server in a different group with a different security level.

Three different security levels:
- noAuthnoPriv - No authentication and no privacy. No authentication password is exchanged and the communications between the agent and the server are not encrypted.
It doesn't use a community string and still uses a username. The username replaces and works the same as the community string in SNMPv1 and v2. Therefore, it doesn't give you an advantage over the old SNMP versions.
- AuthNoPriv - Password authentication is used. The NMS server and the network device will securely authenticate each other and the authentication is encrypted.
The username and password are encrypted, but after the initial authentication, no encryption is used for communications between the devices. So, if the server pulls some information from the device, it will go over the network unencrypted.
- AuthPriv - Password authentication is used and the communication between the agent and the server are also encrypted.
The NMS server and the device are going to securely authenticate each other and whenever they're sharing information, it will be encrypted. Most likely we're going to be using AuthPriv which is more secured.
SNMPv3 Configuration - Group
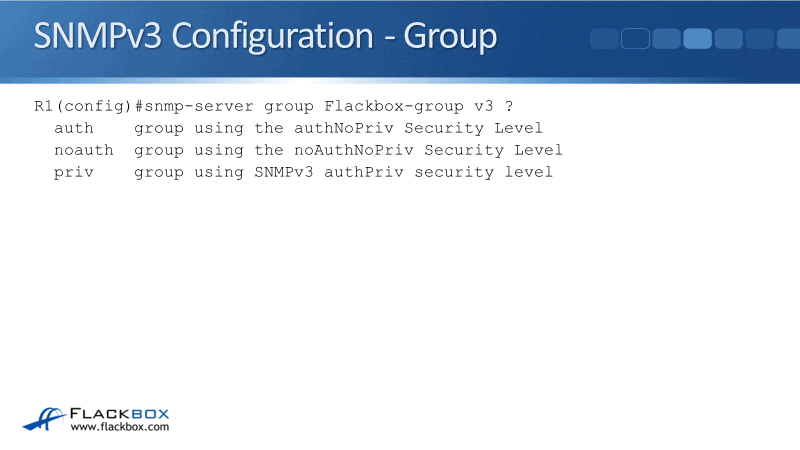
Earlier in this lecture, we discussed that we’re going to have the group and the user as well. Let's configure the group first. In global config mode we’ll enter the command:
snmp-server group Flackbox-group v3 ?
Flackbox-group is the group name and v3 indicates that we’re using SNPMv3. In the example, I've hit the question mark for help, to see what the next keyword is. This is where we set the security level of either Auth, noAuth, or Priv.
I'm going to set it to priv because I want the most secure level. Then I've put in the question mark again to see what the next keyword is. The next keywords we've got are access, contest, match, notify, read, and write.
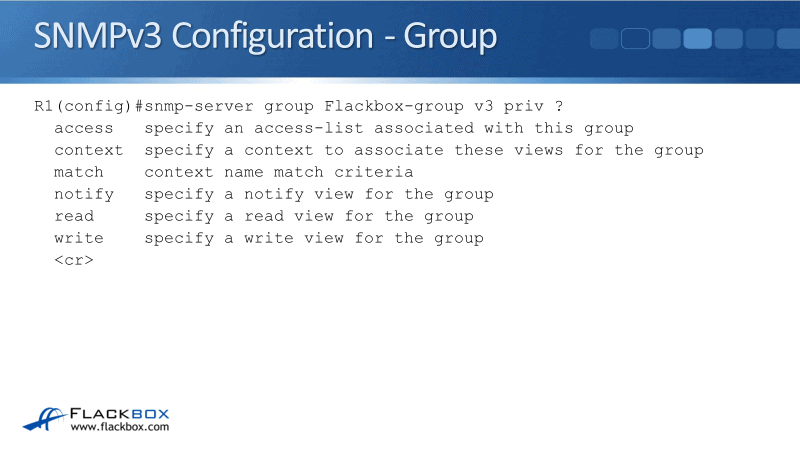
With access, you can set an access list. Context and match both apply to contexts. Notify, read, and write are about views. Let's see what that means:
- Access allows you to configure a normal access list on the router or the switch where you specify the IP address of the NMS server.
When you configure your SNMP settings here, you can reference the access list, meaning you're locking it down with the IP address of your NMS server. This router or switch will only communicate with SNMP with that particular IP address.
- Contexts are used on switches to specify which VLANs are accessible via SNMPs. If you're configuring a switch, you might need to set that up so that your NMS system can access other VLANs, not just the default VLAN.
SNMPv3 Configuration - Views
The last thing we could set is our views. Views can be used to limit what information is accessible to the NMS server. We have read view, write view, and a notify view available. If you don't specify a read view, then all MIB objects are accessible to read.
By default, the NMS server can get all the different SNMP information from that particular device. If you want to lock it down to only be able to pull a particular set of information, then you would use a read view for that.
- Write view. Without explicitly configuring a write view, then no MIB objects are accessible to write. So, if you want it to be able to write anything, then you have to configure a write view.
- Read view locks down what it can read. By default, the NMS server gets read-only access to all MIBs, it can read everything but it can write nothing.
- Notify view is used to send notifications to a member of the group. If you don't specify any, then it will be disabled by default.
SNMPv3 Configuration - Group
When I configure the group here in this example, the full command that I use is:
snmp-server group Flackbox-group v3 priv
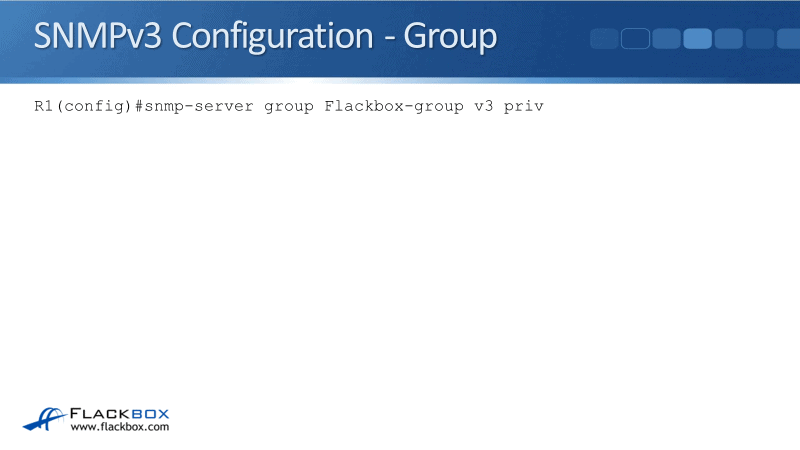
I haven't configured any access lists or any views because they are all optional. I'm using the defaults, therefore, the NMS server in this group will have full read-only access to the device.
SNMPv3 Configuration – User
After configuring the group, next is to configure the user. We will use the command:
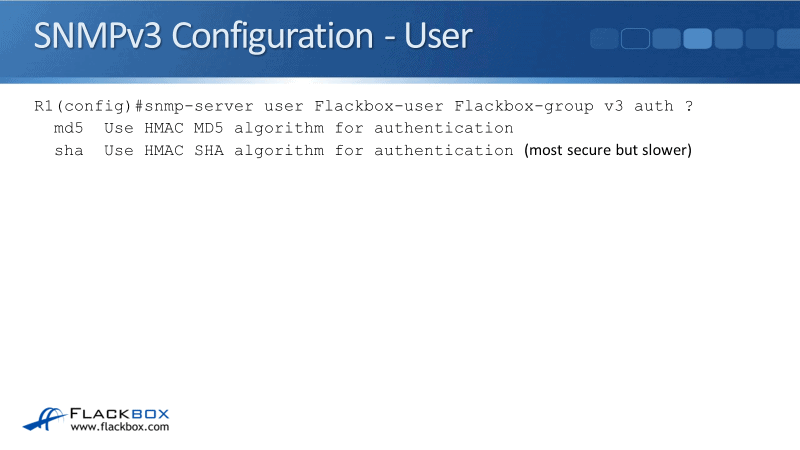
snmp-server user Flackbox-user Flackbox-group v3 auth ?
Flackbox-user is the user name then I specify the group that this user is in and that is Flackbox-group which was configured earlier. The v3 indicates SNMPv3.
The auth command is where I'm going to specify the authentication algorithm that I'm going to use. I can either use MD5 or SHA authentication. SHA is more secure but it's a little bit slower.
So far, our command says:
snmp-server user Flackbox-user Flackbox-group v3 auth sha AUTHPASSWORD priv ?
The authentication password we set is AUTHPASSWORD. We talked about the three different security levels and we specified authentication and privacy separately. Right now, we’ve already configured the authentication.
Next up we’re going to configure the privacy. I entered priv and I've used a question mark again to see the options we have. We can use DES, 3DES, or AES encryption. AES is the most modern and the most secure but it is slower.
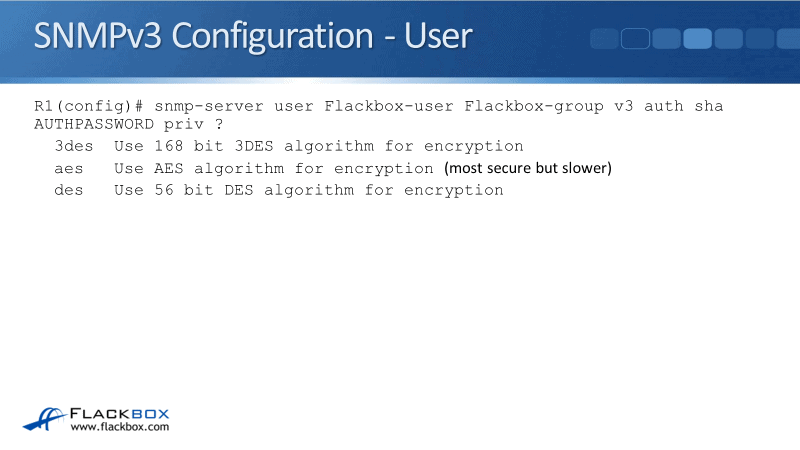
Our command would now be:
snmp-server user Flackbox-user Flackbox-group v3 auth sha AUTHPASSWORD priv aes ?
Next, we would specify whether the encryption would be 128, 192, or 256 bit. The higher the number, the more secure it's going to be. However, it's going to take more CPU cycles thus, becoming a little slower.
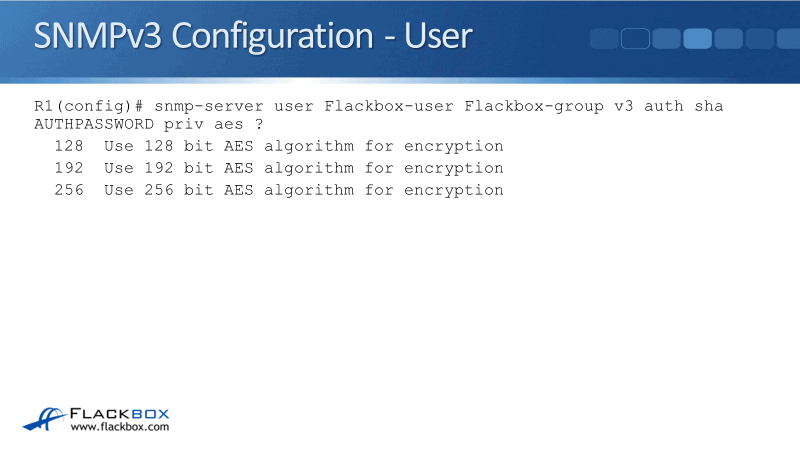
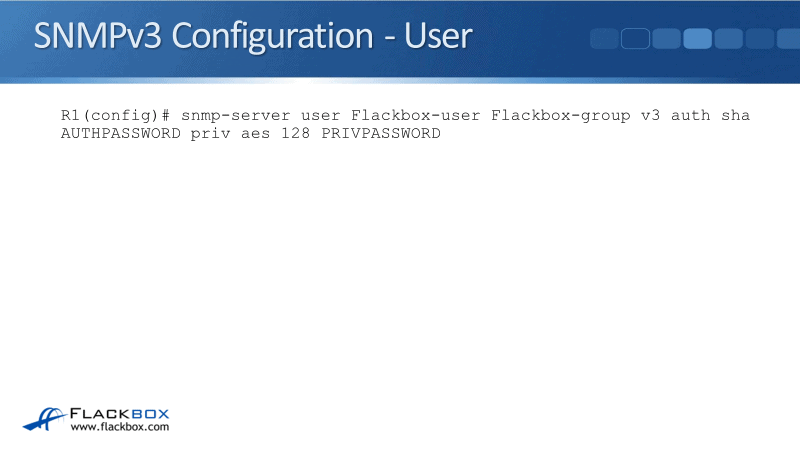
Our full command would be:
snmp-server user Flackbox-user Flackbox-group v3 auth sha AUTHPASSWORD priv aes 128 PRIVPASSWORD
For priv, I'm using aes 128-bit encryption with a password of PRIVPASSWORD. So, that’s my user and my group configuration on my router or switch.
What I would do next is to go onto my NMS server and configure a user there with matching settings here. I would set it with the same username, Flackbox-user. I would specify the auth password and priv password. And DONE. The NMS server is now going to be able to access my device and pull information from it.
SNMP v3 Configuration Example
This configuration example is taken from my free ‘Cisco CCNA Lab Guide’ which includes over 350 pages of lab exercises and full instructions to set up the lab for free on your laptop.
Click here to download your free Cisco CCNA Lab Guide.

Additional Resources
SNMP Concepts and Configuration: https://www.ciscopress.com/articles/article.asp?p=1730888
Chapter: SNMP Version 3: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/configuration/xe-3se/3850/snmp-xe-3se-3850-book/nm-snmp-snmpv3.html
Libby Teofilo

Text by Libby Teofilo, Technical Writer at www.flackbox.com
Libby’s passion for technology drives her to constantly learn and share her insights. When she’s not immersed in the tech world, she’s either lost in a good book with a cup of coffee or out exploring on her next adventure. Always curious, always inspired.